Suorittimen käskykannoista¶
Osaamistavoitteet: RISC- ja CISC-käskykantatoteutusten erityispiirteet ja niiden vertailu.
Suorittimien käskykannoissa ja niihin liittyvästi toteutuksissa ja mikroarkkitehtuureissa on ollut vallalla 1980-luvulta asti kaksi erilaista suuntausta, jotka käsittelemme pääpiirteissään seuraavassa.
CISC¶
CISC (engl. Complex Instruction Set Computer) arkkitehtuureissa ajatuksena on laaja konekielen käskykanta, jonka käskyt ovat itsessään mahdollisimman monipuolisia. Historiallisesti ajatuksena oli, että konekielen käskyt lähestyisivät korkean tason ohjelmointikielen käskyjä, tarjoten niille suoran hardistuen.
Näin käskyihin ja ohjelmaan saadaan tehokkuutta sitä kautta, että ne voivat suorittaa kompleksisia operaatiota yhdellä käskyllä, esimerkiksi salausavaimen luominen. Etuna on myös, että ohjelman toteuttamiseen tarvitaan vähemmän konekielen käskyjä. Tästä esimerkkinä, CISC-käskyt voivat operoida suoraan muistin kanssa ilman että data ensin haetaan rekistereihin.
CISC näin olen monimutkaistaa mikroarkkitehtuuria ja CISC-käskyt onkin yleisesti toteutettu mikro-ohjelmina, joita ajetaan liukuhihnan sisäisesti (engl. multiple cycle / pass computer). Kuvassa alla periaate, jossa liukuhihnan Decode-vaiheesta suoritetaankin käskyä vastaavat mikro-ohjelman käskyt joiden tulos syötetäänkin Execute-vaiheeseen ALU:lle operandeina.
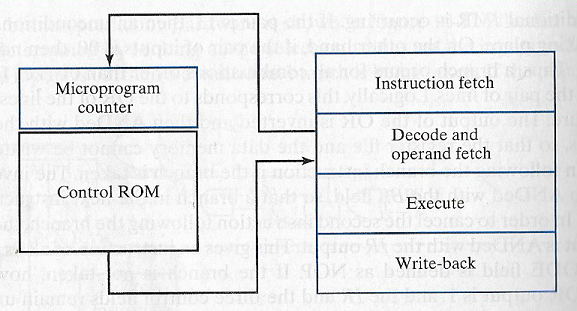
Mikro-ohjelmien toteutus taas voidaan tehdä joko suorittimen konekielellä tai laitteistokuvauskielillä.
CISC-käskykanta-arkkitehtuurin piirteitä:
- Käskyjä sekä yksinkertaisten että kompleksisten operaatioiden suorittamiseen
- Käskyn operaatiokoodi kertoo, onko käsky mikro-ohjelma
- Seurauksena käskyn pituus (tavuina) vaihtelee paljon
- Useita erilaisia osoitusmuotoja
- Käskyt voivat tehdä suoria muistiosoituksia
- Käsky voi operoida jopa muistialueen kanssa, eikä yhden muistiosoitteen osoituksia kerrallaan
- Käskyjen suoritusaika vaihtelee suuresti
- Suoritusaika voi olla jopa satoja kellojaksoja..
Haittapuolena CISC-käskykannassa on mainittu monimutkainen mikroarkkitehtuurin toteutus suorittimissa. Myös mikro-ohjelma saattaa vaatia, että liukuhihnan vaiheita suoritetaan useaan kertaan silmukassa, eli siis ikäänkuin yhden konekielen käskyn sisällä, jolloin suoritusaika pitenee. Lisäksi (okei, joskus aiemmin) korkean tason kielten kääntäjät eivät ole aina osanneet hyödyntää CISC-käskyjä tehokkaasti.
Toteutuksia¶
Nykyisten PC-tietokoneiden suorittimet perustuvat pitkälti Intelin CISC-käskykanta-arkkitehtuuriin. Esimerkiksi juurikin x86-prosessoriperheessä on aina uuden sukupolven myötä lisätty uusia CISC-pohjaisia käskyjä. Nykyään koko Intelin käskykannan selittävä dokumentaatio koostuu kolmesta osasta ja on tuhansia sivuja pitkä..
Esimerkki x86:sen CISC-käskykannasta, jossa kahdella käskyllä repne (repeat if not equal) ja scasb saadaan etsittyä merkki merkkijonosta.
# Etsi merkin 'e' paikka merkkijonossa my_string mov ecx,my_string_len mov edi,my_string mov al,'e' cld repne scasb
Esimerkki. Motorolan 68000-prossun CISC-käskykannasta, jossa yhdellä siirtokäskyllä voidaan siirtää useiden rekisterien data kerralla ja samaan aikaan tehdään aritmeettinen operaatio.
# Siirrä sana (w) rekisterin a0 osoittamasta muistipaikasta a1:sen osoittamaan muistipaikkaan # ja kasvata rekisterien arvoja sanan verran move.w (a0)+,(a1)+ # Siirrä 32-bittiset rekisterit (l) d0, d4-d7 ja a2-a6 pinoon, mutta ensin siirrä pino-osoitinta (sp) movem.l d0/d4-d7/a2-a6,-(sp)
RISC¶
RISC (engl. Reduced Instruction Set Computer)-käskykanta perustuu ajatukseen, että suorittimen tehokkuus haetaan yksinkertaisilla (ja siten nopeilla) konekielen käskyillä. Tämä johtaa suorittimessa yksinkertaisempaan toteutukseen, ohjauslogiikkaan ja mikroarkkitehtuuriin. RISC-arkkitehtuurissa käsky suoritetaan yhdellä liukuhihnan läpäisyllä (engl. single cycle/pass computer).
RISC:n syntyyn johti huomio, että CISC-käskyt eivät aina tuottaneet nopeinta suoritusta, vaan käskyn jakaminen pienempiin osiin nopeuttaisi suoritusta vielä enemmän ja/tai parantaisi suoritustehoa (IPS) kokonaisuudessaan, koska CISC-käskyjen liukuhihnatoteutukset ovat haastavia.
RISC-arkkitehtuurin piirteitä:
- Käskykanta koostuu yksinkertaisista käskyistä, jotka tekevät pienen operaation kerrallaan
- Liukuhihnatoteuksella hyvä suoritusteho (engl. throughput)
- Mahdollistaa joustavasti konekielisen ohjelman toteutuksen kun toiminnallisuudet voidaan toteuttaa eri tavoilla
- Ohjelmakoodin optimointi on haastavampaa ja jää usein kääntäjän vastuulle
- Käskyjen pituus sama kaikissa käskyissä
- Voi sisältää vakioarvoina muistiosoitteita
- Käskyjen operandeina käytetään pääosin rekistereitä
- Nopea suoritus, kun operoidaan vain rekistereiden kanssa
- Käskykannassa muistiosoitukset rajoitettu vain erillisille load / store-käskyille
- Voidaan saavuttaa vakioitu suoritusaika
- Minimoidaan (hitaat, > 1 kellojakson) muistiosoitukset
- Käytössä paljon rekistereitä, jotta saadaan enemmän dataa lähelle suoritinta.
- Esimerkiksi AVR-arkkitehtuurissa (mm. 8-bittiset Arduinot) suorittimessa on 32 yleiskäyttöistä rekisteriä.
- Data-hasardit kalliita!
- Osoitusmuotoja rajoitetusti
- Suoraa (engl. immediate) osoitusta suositaan, jolloin minimoidaan osoitteen tulkintalogiikka
Toteutuksia¶
Sulautetuissa järjestelmissä ja signaalinkäsittely-prosessoreissa (DSP) suositaan RISC-arkkitehtuuria, esimerkiksi tunnettu ATmelin AVR-arkkitehtuuri on selkeästi RISC. Kts. myös johdanto-kappaleessa esitetty assembly-kielinen silmukkakoodi. Mitä RISC-piirteitä löydät koodista??
Modernissa PC-maailmassa CISC-käskykantaa itseasiassa puretaan RISC-käskyiksi suorittimen sisäisellä lisädekooderilla (esimerkiksi AMD:n K5-suoritimessa). On esitetty, että yhden x86-CISC-käskyn toteuttamiseksi tarvitaan 3-4 RISC-käskyä. Tuloksena yksinkertaisempien RISC-käskyjen suoritusta on sitten helpompi liukuhihnoittaa, jota kautta suoritusteho kasvaa.
Intelin Pentium-suorittimet parinkymmenen vuoden takaa ovat RISC-pohjaisia (3 miljoonaa transistoria). Kuten edellisessä materiaalissa esitettiin, Pentiumeissa on kaksi liukuhihnoitettua kokonaislukusuoritinta (itseasiassa suoritinperheen aiempaa mallia 80486) ja lisäksi liukuhihnoitettu (8-vaihetta) liukulukusuoritin. Suorittimen ohjausosassa on Instruction Pairing-logiikkaosa jakamassa kaksi käskyä yhtaikaa suoritettavaksi. Pentiumeissa (CISC-)käskyt puretaan RISC-mikro-operaatioiksi.

Esimerkki. Ylläesitetyt 68000-prosessorin käskyt olisi helposti purettavissa RISC-käskyiksi?
Esimerkki. Yliopistomaailmassa (Berkeleyn yliopisto, 2010) on kehitetty avoin RISC-käskykanta-arkkitehtuuri RISC-V, jota voi kuka tahansa vapaasti käyttää suoritintoteutuksessaan. Muunmuassa massadata-analyysiin ja grafiikkasuorittimiin on jo olemassa/tulossa RISC-V-pohjaisia toteutuksia.
CISC vs RISC¶
Allaolevassa taulukossa kootusti CISC- ja RISC-arkkitehtuurien eroja.
| CISC | RISC |
| Paljon monimutkaisia käskyjä | Vähän ja yksinkertaisia operaatioita suorittavia käskyjä (tyypillisesti alle 100) |
| Käskyissä vaihteleva (pitkä) suoritusaika | Käskyillä lyhyt vakioitu suoritusaika |
| Konekielen käskyn pituus 1-15 tavua (x86) | Konekielen käskyn pituus sama kaikissa käskyissä (tyypillisesti 2-4 tavua) |
| Muistiosoituksille ja operandien esitykselle useita osoitusmuotoja (siirtymiä, indeksointia) | Yksinkertaiset suorat osoitusmuodot ja paljon rekistereitä |
| ALUn operaatiot suoraan sekä rekistereille että muistille | ALUn operaatiot vain rekistereille. Erilliset käskyt datan lukemiseksi ja kirjoittamiseksi muistiin |
| Käskyt asettavat automaattisesti prosessorin tilabitit | Ei (välttämättä) tilabittejä, suorituksen tulos näkyvissä yleisissä rekistereissä |
| Pinoa käytetään paljon argumenttien ja muistiosoitteiden tallennukseen | Argumentit ja muistiosoitteet rekistereissä, halutaan välttää muistiosoituksia |
| Suoritintoteutuksen yksityiskohdat piilossa ohjelmoijalta | Toteutus heijastuu konekieliseen ohjelmaan. Rajoituksia mitä ja miten voi toteuttaa |
Lopuksi¶
Nykyään suoritinarkkitehtuureissa on toteutettu parhaat puolet molemmista arkkitehtuurimalleista ja asiaan palaammekin myöhemmässä materiaalissa..
Kurssimme toisen oppikirjan kirjoittajat David Patterson ja John Hennessy ovat itseasiassa ensimmäisinä esittäneet ja kehittäneet RISC-arkkitehtuurimallia 1970-80 -luvuilla.
Anna palautetta
Kommentteja materiaalista?